
This one starts the series of more challenging puzzles. The binary is actually a key logger with a twist, writing every pressed key into a log file.
Fig. 1
It will try to install itself in your system under %SystemRoot% by disguising as svchost.dll. It will also add itself under Run key to ensure persistence (boring). The interesting things are waiting for us latter on.
As I mentioned previously, this key-logger has a twist – each key press is monitored by GetAsyncKeyState which is running in the loop.
Flare-On 2014 Chellage 6

Challenge #6, probably the most toughest task among the series. We are blessed with 64 bit statically linked ELF file with stripped symbols. During the challenge we will be using the following tools:
radare2 IDA gdb First things, first Let’s execute the file (in VM of course) and see what will be the output (if any):
[test ~]$ ./c6 no Not much, but it’s a start. This no will be our anchor and starting point in a minute.
Necurs Kit Privilege Escalation Study
Recently there were several new posts (FSecure Post and Peter Ferrie) about updates to the Necurs malicious kit which in essence is based on the malicious driver with sole purpose to protect other malware from security products. The updated version is now shipped as an embedded self-contained launch-and-forget shellcode which will drop the appropriate driver according to the underlingg OS and on successful deployment will start immediate protection. The authors of the kit will supply the client several APIs that could be used to operate the driver.
Malware reuse - cpu emulation for malware analysis
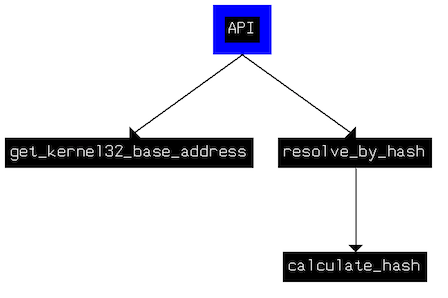
During any RE project, precise goal definition is one of the most important steps, without which the project will most likely fail. And I’m not even talking about how time consuming it could be, as frequently I can find the rabbit hole but I’m not really aware how deep it goes. The context for the whole post is RE of malicious software and here I’d like to talk a little bit about the way to put some of the work on the shoulders of the malware itself and still be able to concentrate on the main goals.
Banker Challenge - another solution
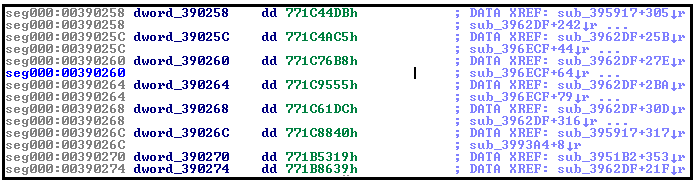
In my last post I presented a malware analysis solely based on the dynamic technique using OllyDbg. The goal was to recover the algorithm that was used for domain name generation of the C&C server. Knowing, that there is no one best tool for everything but rather the best tool for a particular problem, I’ve decided to try and solve the same challenge with the help from static analysis tools, like IDA (free edition), while minimizing Olly involvement.