This one starts the series of more challenging puzzles. The binary is actually a key logger with a twist, writing every pressed key into a log file.
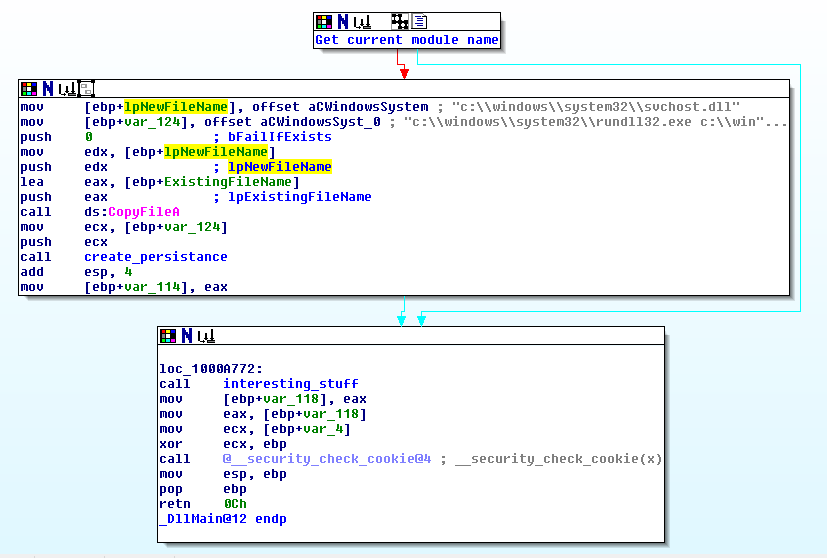
Fig. 1
It will try to install itself in your system under %SystemRoot% by disguising as svchost.dll. It will also add itself under Run key to ensure persistence (boring). The interesting things are waiting for us latter on.
As I mentioned previously, this key-logger has a twist – each key press is monitored by GetAsyncKeyState which is running in the loop. Once the pressed key generated a character, it will be passed to a processing switch statement:
Fig. 2
The twist here is that the “secret” message was encoded by the means of flags that in the beginning all are initialized by init_secret_flags. Each flag represents the letter in the final “secret” message and the keys must be pressed in the particular order.
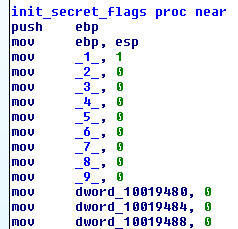
Fig. 3
If there is an error in the sequence, for example pressing 4, everything will be reset (Fig.4 – 2) – init_secret_flagscalled again. On the other hand, i will be somewhere in the final “secret” message (Fig. 4 – 3) as the next flag is set to ‘on’ state.
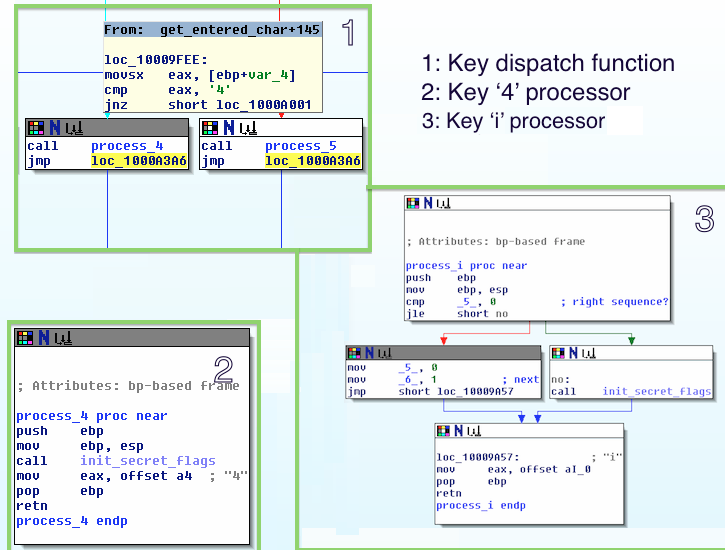
Fig. 4
The way to solve this puzzle is rather simple – just follow the flags in IDA (for example, using XRefs) where the particular flag is compared with 0 and write down the letter that is processes by that function. Pay attention, that the first flag is already set in init_secret_flags. Let’s walk the process for first 2 characters:
- find reference for first flag where it is compared with 0
- write down the character (‘l’)
- find reference for second flag where it is compared with 0
- write down the character (‘0’ – zero)
![]()
Fig. 5
Once done, you should see the following: