This challenge is about analyzing a binary file. Using IDA. we see here a sort of “obfuscation” where the actual code (payload) is moved into the stack by the loader and executed from there:
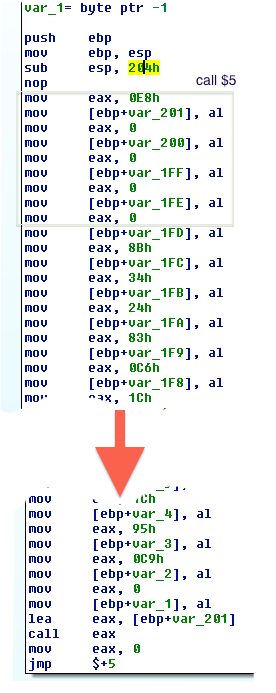
The payload is actually a multi-stage xor based, self decrypting code which in our case has various funny sentences revealed in every decrypted part:
| Stage | Result |
|---|---|
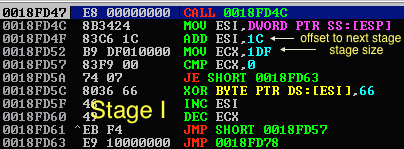 |
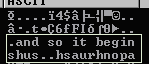 |
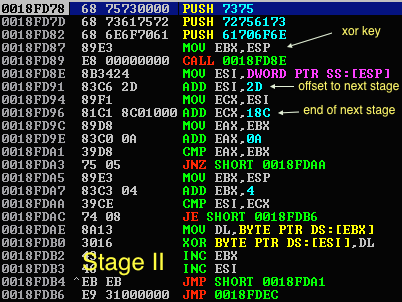 |
 |
I hope, you’ve got the idea here. I’ll omit several stages and come straight to the last meaningful stage where the email we’ve been looking for is revealed:
