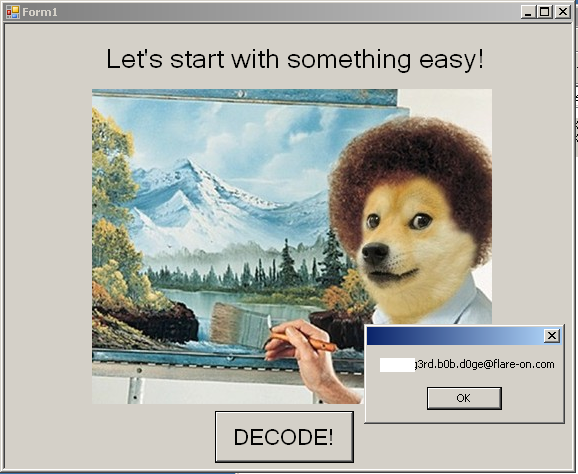
The binary can be downloaded from the original site. Quick check shows that this is a .NET executable with some humor:
Using very handy .NET decompiler, ILSpy, let’s check the source of this funny thing with emphasis on the implementation of Decode event handler:
private void btnDecode_Click(object sender, EventArgs e)
{
this.pbRoge.Image = Resources.bob_roge;
byte[] dat_secret = Resources.dat_secret;
string text = "";
for (int i = 0; i < dat_secret.Length; i++)
{
byte b = dat_secret[i];
text += (char)((b >> 4 | ((int)b << 4 & 240)) ^ 41);
}
text += "\0";
string text2 = "";
for (int j = 0; j < text.Length; j += 2)
{
text2 += text[j + 1];
text2 += text[j];
}
string text3 = "";
for (int k = 0; k < text2.Length; k++)
{
char arg_B6_0 = text2[k];
text3 += (char)((byte)text2[k] ^ 102);
}
this.lbl_title.Text = text3;
}
The evident thing here is the presence of Resources.dat_secret which holds the solution to the challenge. So, here we have text, text2 and text3 which will probably have the email I’m looking for. One can solve the challenge by writing some code which will decode the resource and reveal the secret. But, I say, if the decoder is already written in this case and in front of me, why no use it :–).
I just add some MessageBox calls to the code and recompile it back. This will show me the variables!
private void btnDecode_Click(object sender, EventArgs e)
{
...
for (int i = 0; i < dat_secret.Length; i++)
{
byte b = dat_secret[i];
text += (char)((b >> 4 | ((int)b << 4 & 240)) ^ 41);
}
text += "\0";
MessageBox.Show(text);
...
MessageBox.Show(text2);
}
Here is the resulting email. I’ll leave the final discovery to you :–)